Monitored Services
Background
Any computer system that is exposed to the internet risks being maliciously attacked through repeated attempts to login to the system, often refered to as brute force attacks. Brute force attackers will repeatedly guess new username/password combinations in an attempt to gain unauthorized access to the system. The IP Block List feature has been added to the UCX software to reduce the potential impact of these brute force attacks by temporarily blocking the connection requests originating from those IP addresses associated with repeated incorrect login attempts. Control of what services are monitored and the threshold criteria for determining when and for how long to block addresses is provided on the Monitored Services page.
The IP Block List feature is automatically installed and enabled through the standard UCX Software Update process.
Monitored Services
The UCX software can monitor login attempts for the following services:
- Telephony: monitors IP Addresses attempting to connect using some of the common protocols associated with UCX telephony;
- Secure Shell: monitors IP Addresses attempting to connect to the UCX using SSH protocol
- Web Server: monitors IP Addresses attempting to connect to the UCX web server
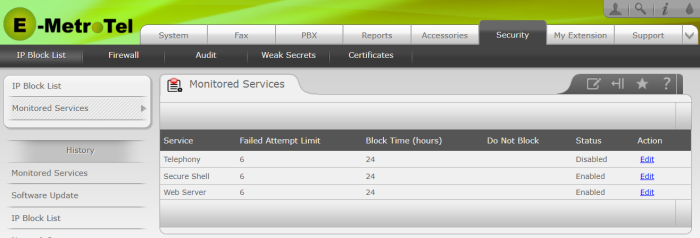
Action: Edit
Clicking the Edit button associated with any of the Monitored Services will allow you to change the Failed Attempt Limit, Block Time, Do Not Block entries, and the monitoring Status of that service.
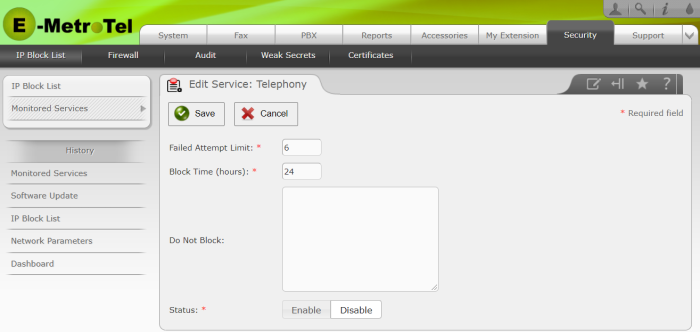
Failed Attempt Limit: The number of consecutive times that an endpoint can enter incorrect credentials before being placed on the IP Block List. (Default = 6 attempts)
Block List Time (hours): The length of time that the endpoint will be blocked from access the service. (Default = 24 hours)
Do Not Block: A list of IP Addresses and or subnets that are manually entered (one per line) that will never be blocked from accessing this service. Subnets must be entered using standard CIDR notation (e.g., 192.168.1.0/24).
Status: You can Enable or Disable each of the individual Monitored Services.


